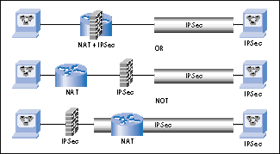
Discuss some of the problems NATs create for IPsec security. (See [Phifer 2000]). Can we solve these problems by using IPv6? Why deployment of IPv6 has been slow to date. What is needed to accelerate its deployment?
We must always remember that the point of IPSec is not just to protect the confidentiality of the data, but also to assure the authenticity of the sender and the integrity of the data. Both IPSEC and NAT together mean the problem with NAT is obvious: NAT must change information in the packet headers in order to do its job.
The first problem which occurs with Nat is that, it changes the IP address of the internal computer to that of the NAT device. The Internet Key Exchange (IKE) protocol which is used by IPSec encloses the sending computer’s IP address in its payload, and this enclosed address doesn’t match the source address of the IKE packet (which is that of the NAT device). If these addresses are not matching the receiving computer in that it will drop the packet.
NAT changes the way IP works at a fundamental level. NAT lets you hide networks and hosts in a variety of ways. Likewise, IPsec is your friend because you can securely connect your remote office
What We Offer:
• On-time delivery guarantee
• PhD-level professionals
• Automatic plagiarism check
• 100% money-back guarantee
• 100% Privacy and Confidentiality
• High Quality custom-written papers